MX load balancing is the practice of distributing inbound email across multiple mail exchangers using MX records, DNS, and/or Layer 4 load balancers to improve availability, performance, and spam resilience. By publishing multiple MX hosts or placing an SMTP load balancer in front of them you enable automatic failover, parallel processing of mail, and a more reliable mail flow.
Inbound mail or MX load balancing ensures your domain can receive email even during server failures or spikes in traffic. In this guide, I’ll explain how MX load balancing works, the best architectures to deploy, configuration examples, common pitfalls, and practical testing tips, based on 12+ years building and operating mail systems for hosting and SaaS environments.
What is MX Load Balancing?
MX load balancing distributes SMTP connections to more than one receiving server. You can achieve it in three main ways:
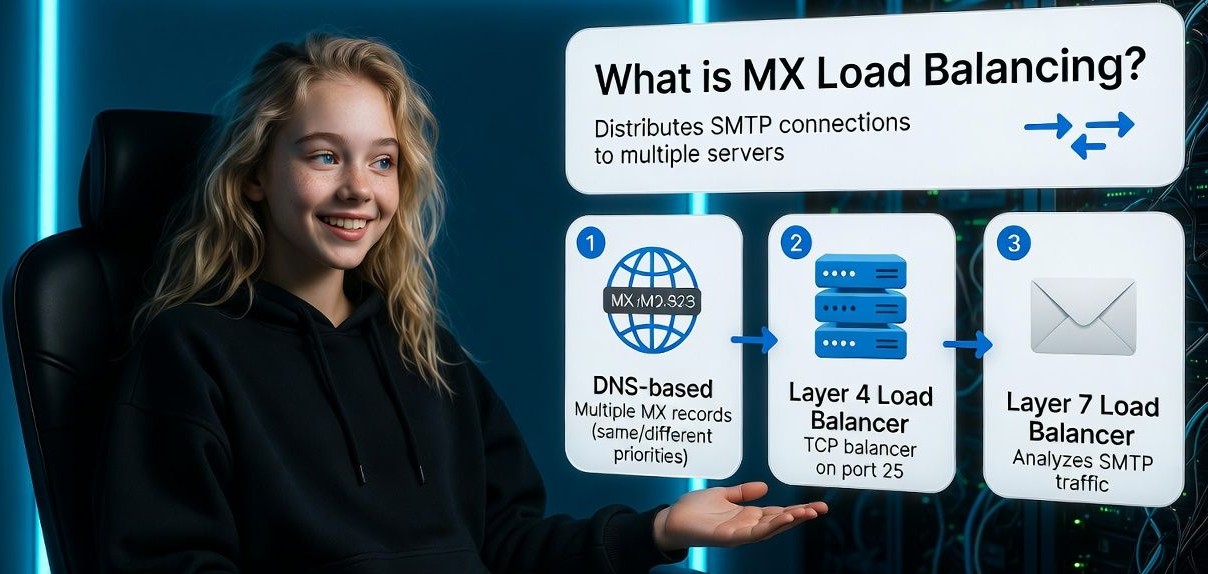
- DNS based: Publish multiple MX records with the same or different priorities.
- Layer 4 load balancer: Place a TCP load balancer in front of SMTP endpoints (ports 25/587/465).
- Anycast/Edge filtering: Use globally distributed filtering or security gateways that hand off clean mail to your core mailstore.
The result is higher availability, horizontal scale for spam filtering and delivery, and seamless failover if one server or site goes down.
How MX Load Balancing Works (DNS, SMTP, and Retries)
Inbound SMTP relies on DNS MX records to discover your mail exchangers. Sending MTAs resolve your domain’s MX set, sort by priority (lowest first), then attempt delivery. If a target is down or returns a temporary 4xx, they retry other MX hosts, queue locally, and attempt redelivery following SMTP backoff rules.
Priority vs. Equal Priority MX
Different priorities usually imply failover: senders try the lowest number first and only use higher numbers if the primary is unavailable. Equal priority MX records enable pseudo–round robin because senders often randomize among equals. This provides basic load distribution without a dedicated load balancer.
Common Architectures for Inbound Mail HA
1) DNS Only Load Balancing (Multiple MX)
Publish two or more MX records pointing to separate SMTP gateways or filtering appliances. Use equal priority for distribution, or primary/secondary for active–passive failover. Keep TTLs reasonable (e.g., 300-1800 seconds) so changes propagate quickly but don’t overload resolvers.
2) Layer 4 TCP Load Balancer in Front of MTAs
Place an L4 load balancer (HAProxy, NGINX Stream, AWS NLB, etc.) in front of multiple SMTP servers. The MX points to the load balancer VIP, which evenly spreads connections using algorithms like round robin or least connections. Health checks remove bad backends instantly.
3) Edge Filtering + Mailstore Separation
Terminate inbound mail on filtering clusters (spam/virus/DLP) at the edge, then relay clean mail to internal mailstores (Exchange, Postfix/Dovecot, Zimbra). This scales filtering independently of storage and lets you geo balance edges while keeping core mailboxes centralized.
Best Practices for MX Records and DNS
Naming, TTLs, and Priority
Use stable hostnames (e.g., mx1.example.com, mx2.example.com). Set a moderate TTL (300-1800 seconds) on MX and A/AAAA records. If you need load distribution, prefer equal priority MX; for strict failover, use distinct priorities (e.g., 10 and 20).
A/AAAA Balance and Anycast
If an MX hostname has multiple A/AAAA records, senders may also randomize across them. For global performance, Anycast on edge gateways can shorten TCP round trip and improve spam absorption under volumetric attacks.
Security and Policy Considerations
Load balancing shouldn’t weaken security. Apply consistent controls across all MX hosts:
- Mandatory TLS for receiving when possible; advertise STARTTLS correctly.
- SPF, DKIM, and DMARC validation on the first hop that accepts mail from the internet.
- MTA-STS and TLS-RPT for upgraded transport security and reporting.
- DANE for TLS authentication where DNSSEC is deployed.
- Greylisting, throttling, tarpitting, and RBL checks at the edge to deflect abuse.
Ensure all MX servers share the same policy and blocklists so senders get consistent outcomes, reducing retry storms and false positives.
Pros and Cons of Each Approach
DNS Only (Multiple MX)
- Pros: Simple, no single point of failure, leverages SMTP retry logic, low cost.
- Cons: Uneven distribution across senders, slower failover if TTLs are high, limited visibility/control.
L4 Load Balancer
- Pros: Fine grained control, instant failover, health checks, session distribution.
- Cons: Additional component to manage; requires HA setup for the balancer itself.
Edge Filtering Gateways
- Pros: Offloads spam/malware, improves performance, scales independently, can be Anycast.
- Cons: More moving parts, needs reliable routing to internal mailstores.
Configuration Examples (DNS, HAProxy, Testing)
DNS Zone with Multiple MX (BIND)
$TTL 900
@ IN SOA ns1.dns.example. hostmaster.example. (
2026010101 ; serial
3600 ; refresh
600 ; retry
1209600 ; expire
300 ) ; minimum
; Equal-priority for distribution
@ IN MX 10 mx1.example.com.
@ IN MX 10 mx2.example.com.
; Host addresses
mx1 IN A 203.0.113.10
mx2 IN A 203.0.113.20
; Optional IPv6
mx1 IN AAAA 2001:db8::10
mx2 IN AAAA 2001:db8::20HAProxy as an SMTP Load Balancer (TCP Mode)
global
log 127.0.0.1 local0
daemon
maxconn 50000
defaults
log global
mode tcp
option dontlognull
timeout connect 5s
timeout client 2m
timeout server 2m
frontend smtp_inbound
bind *:25
mode tcp
option tcplog
default_backend smtp_backends
backend smtp_backends
mode tcp
balance leastconn
option smtpchk HELO lb.example.com
server mta1 10.0.0.11:25 check fall 2 rise 2
server mta2 10.0.0.12:25 check fall 2 rise 2Point your domain’s MX to the load balancer’s public IP/hostname. Health checks ensure failed MTAs are removed within seconds, delivering fast failover beyond DNS based methods.
Testing Commands
# Inspect MX records
dig +short MX example.com
nslookup -type=mx example.com
# Trace connection path
telnet mx1.example.com 25
openssl s_client -starttls smtp -connect mx1.example.com:25 -servername mx1.example.com
# Send a test via swaks (handy MTA tester)
swaks --to you@example.com --server mx1.example.com --ehlo test --tlsOperational Tips from the Field
- Keep identical SMTP banners, TLS ciphers, and policies across all MX hosts for consistent sender experience.
- Measure queue depth, 4xx/5xx rates, TLS negotiation failures, and average SMTP session time.
- Greylisting can amplify retries; tune it carefully on distributed edges to avoid unnecessary delays.
- If filtering occurs at the edge, use authenticated relays or internal allowlists to protect the mailstore from bypass.
- Document failover behavior: what happens if a site goes down, and where queued mail resides.
Common Mistakes to Avoid
- Uneven MX policies (e.g., STARTTLS on one server, not on another).
- MX hosts pointing to the same single point of failure behind the scenes.
- Overly long TTLs that delay cutovers during incidents.
- Ignoring IPv6 many senders prefer or attempt IPv6 first.
- No health checks or logging at the load balancer layer.
Use Cases and Patterns
- Small businesses: Two equal priority MX hosts on different VMs or regions for simple resilience.
- Enterprises: Edge filtering cluster (Anycast) relaying to regional mailstores with L4 balancing per site.
- SaaS providers: Multi region MX with traffic steering and automated capacity scaling during campaigns.
- Compliance heavy orgs: Layered gateways with DLP/archiving, strict TLS policies, and MTA-STS.
When to Use a Managed Provider
If you don’t want to engineer and monitor SMTP edges, consider managed email gateways or hosting. At YouStable, we design and operate highly available inbound mail stacks redundant MX, L4 load balancing, Anycast edge filtering, and 24×7 monitoring, so your domain keeps receiving mail, even during spikes or outages.
Checklist: Implementing MX Load Balancing
- Define goals: distribution, failover, security, or all three.
- Choose approach: equal priority MX, priority based failover, or L4 load balancer.
- Set consistent SMTP/TLS/security policies across all edges.
- Configure health checks and monitoring (queues, errors, TLS).
- Test regularly: DNS, SMTP banners, STARTTLS, retries, and failover scenarios.
- Document procedures and review TTLs for incident readiness.
FAQs
Does an MX record automatically provide load balancing?
Partly. Multiple MX records of equal priority encourage senders to distribute connections, but behavior varies by sending MTA. For predictable distribution and instant failover, use a TCP load balancer with health checks.
What MX priority should I use for failover?
Use a lower number for primary (e.g., 10) and a higher number for secondary (e.g., 20). Senders try the lowest first and only use higher priorities if the primary is unavailable or returns a temporary failure.
Is Layer‑4 load balancing safe for SMTP and TLS?
Yes. SMTP is a TCP protocol, and STARTTLS occurs within the TCP session. L4 balancers forward packets transparently without terminating TLS, preserving end to end encryption and simplifying compliance.
How do I test MX load balancing and failover?
Use dig/nslookup to view MX records, telnet/openssl to verify SMTP/STARTTLS, and swaks to send test messages. Simulate node failures while watching queue depth, connection distribution, and delivery outcomes to ensure behavior matches expectations.
What TTLs should I set for MX records?
Common values range from 300 to 1800 seconds. Shorter TTLs help during incidents or migrations, while longer TTLs reduce resolver queries. Align TTLs with your change frequency and incident response plan.
Whether you’re scaling a growing operation or hardening a mission critical environment, MX load balancing is your foundation for dependable inbound mail. If you want a turnkey, battle tested setup, YouStable can architect and manage it end to end so your email is always on.