A load balancer on a Linux server distributes incoming traffic across multiple backend servers to improve performance, uptime, and scalability. To use it: choose a tool (HAProxy, Nginx, or LVS/IPVS), configure backends and health checks, enable SSL/TLS if needed, harden security, and monitor traffic. Test failover and performance before going live.
If you’re scaling applications, learning how to use a load balancer on a Linux server is one of the highest-impact steps you can take. In this guide, you’ll set up a production-ready load balancer with Nginx and HAProxy, compare approaches (L4 vs L7), add SSL, sticky sessions, health checks, high availability, and tune for speed and security.
What Is a Load Balancer and Why Use It on a Linux Server?
A load balancer sits in front of your application servers and distributes traffic to prevent overload, reduce latency, and provide high availability. On Linux, common options include Nginx (Layer 7 HTTP/HTTPS), HAProxy (Layer 4/7 TCP/HTTP), and LVS/IPVS (high-performance Layer 4 in-kernel load balancing).
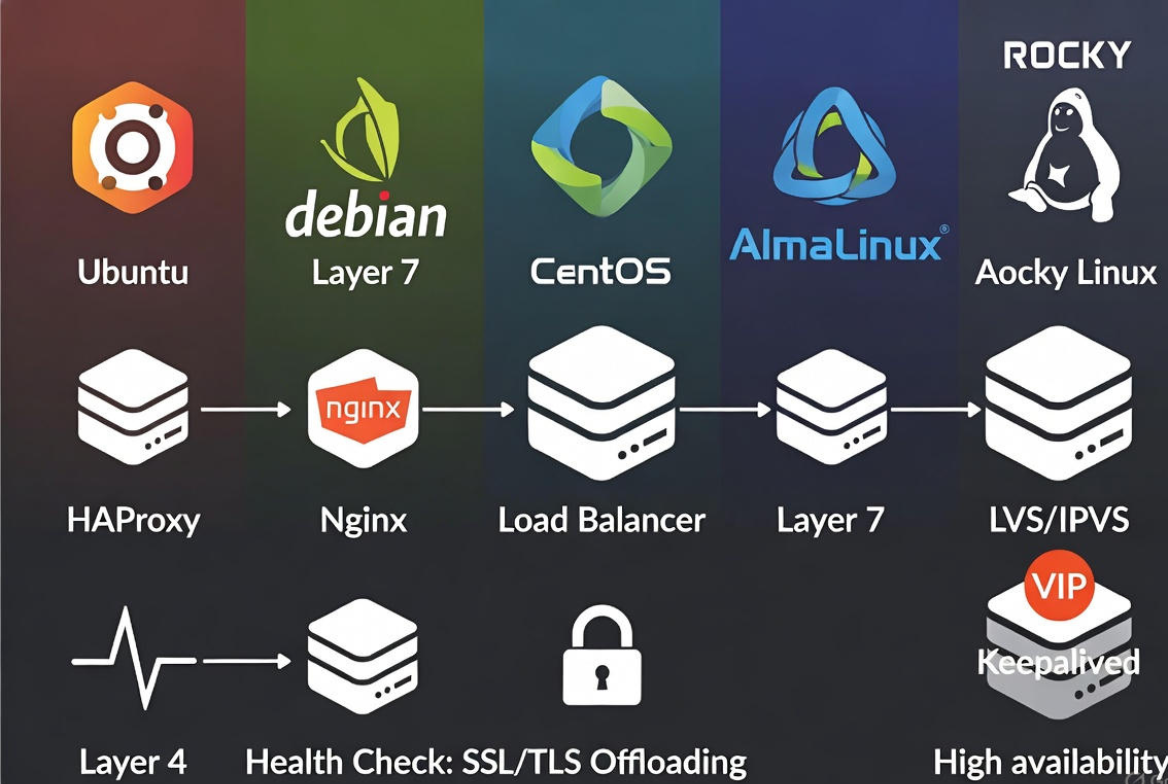
Layer 4 vs Layer 7
Layer 4 (TCP/UDP) forwards connections without inspecting HTTP; it’s extremely fast and simple. Layer 7 understands HTTP/HTTPS and can route by URL, headers, cookies, and handle SSL termination. Choose L4 for raw throughput (e.g., TCP services), L7 for smarter routing (web apps, APIs).
Key Benefits
- High availability: remove failed nodes via health checks
- Scalability: add or remove backend servers seamlessly
- Performance: concurrency, caching layers, TCP reuse
- Zero-downtime deployments: drain nodes and roll out safely
- Security: centralize TLS, WAF, rate limiting (L7)
Choosing a Linux Load Balancer (Nginx vs HAProxy vs LVS/IPVS)
Nginx (Layer 7 HTTP/HTTPS)
Great as a reverse proxy and HTTP load balancer, easy SSL termination, and static file performance. Passive health checks are built-in; active checks require Nginx Plus or third-party modules. Simple to learn and widely supported.
HAProxy (Layer 4/7)
Production workhorse with advanced health checks, detailed stats, TLS offload, stickiness, and high performance. Ideal for dynamic routing, microservices, and demanding traffic patterns.
LVS/IPVS (Layer 4, kernel-level)
IPVS (with Keepalived) provides extremely fast L4 load balancing in kernel space. Best for very high throughput (millions of connections), often paired with HAProxy or Nginx at L7 for HTTP logic.
Which one should you use?
- Web apps/APIs needing SSL, headers, URL routing: HAProxy or Nginx
- Massive L4 throughput (TCP/UDP): IPVS/Keepalived
- Simple reverse proxy to start fast: Nginx
- Advanced health checks and stickiness: HAProxy
Prerequisites and Reference Architecture
- 1–2 Linux load balancer nodes (Ubuntu/Debian/CentOS/Alma/Rocky)
- 2+ application servers (e.g., 10.0.0.11, 10.0.0.12)
- DNS A/AAAA for your domain to the load balancer’s public IP or VIP
- Firewall open: 80/443 to LB, 8404 (optional HAProxy stats), protocol 112 for VRRP (Keepalived)
- System access: sudo, SSH, editor, curl
Quick Start: Nginx Load Balancer (HTTP/HTTPS)
Nginx is a straightforward way to start with an L7 load balancer on a Linux server. Below is a minimal HTTP configuration with least-connections and passive health checks.
# Ubuntu/Debian
sudo apt update && sudo apt install -y nginx
# RHEL/CentOS/Alma/Rocky
sudo dnf install -y nginx
sudo systemctl enable --now nginx# /etc/nginx/conf.d/lb.conf
upstream app_pool {
least_conn;
server 10.0.0.11:80 max_fails=3 fail_timeout=10s;
server 10.0.0.12:80 max_fails=3 fail_timeout=10s;
# For session persistence, consider:
# ip_hash; # Simple stickiness by client IP (not ideal behind NAT)
}
server {
listen 80 default_server reuseport;
server_name example.com;
location / {
proxy_pass http://app_pool;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_connect_timeout 5s;
proxy_read_timeout 60s;
proxy_next_upstream error timeout http_502 http_503 http_504;
}
}sudo nginx -t
sudo systemctl reload nginxTo enable HTTPS quickly with Let’s Encrypt on Nginx:
sudo apt install -y certbot python3-certbot-nginx
sudo certbot --nginx -d example.com -d www.example.com
sudo systemctl reload nginxNote: Active HTTP health checks require Nginx Plus or an external checker. If you need robust checks, prefer HAProxy for the load balancer role.
Quick Start: HAProxy Load Balancer (L4/L7)
HAProxy provides strong health checks, stats, TLS termination, and stickiness—ideal for production web apps and APIs on a Linux server.
# Ubuntu/Debian
sudo apt update && sudo apt install -y haproxy
# RHEL/CentOS/Alma/Rocky
sudo dnf install -y haproxy# /etc/haproxy/haproxy.cfg (minimal but production-friendly)
global
log /dev/log local0
log /dev/log local1 notice
user haproxy
group haproxy
daemon
maxconn 50000
tune.ssl.default-dh-param 2048
defaults
log global
mode http
option httplog
option dontlognull
option http-server-close
option forwardfor
retries 3
timeout http-request 10s
timeout queue 30s
timeout connect 5s
timeout client 60s
timeout server 60s
timeout http-keep-alive 10s
timeout check 5s
frontend http-in
bind *:80
http-response add-header Strict-Transport-Security "max-age=31536000; includeSubDomains" if { ssl_fc }
redirect scheme https code 301 if !{ ssl_fc }
default_backend app
frontend https-in
bind *:443 ssl crt /etc/haproxy/certs/
http-request set-header X-Forwarded-Proto https
default_backend app
backend app
balance leastconn
option httpchk GET /health
http-check expect status 200
cookie SRV insert indirect nocache
server app1 10.0.0.11:80 check cookie s1
server app2 10.0.0.12:80 check cookie s2
listen stats
bind :8404
stats enable
stats uri /
stats realm HAProxy\ Stats
stats auth admin:StrongPass123!For TLS, place PEM files at /etc/haproxy/certs (one .pem per domain, containing fullchain + private key):
# Using Certbot to obtain certs, then combine for HAProxy:
sudo certbot certonly --standalone -d example.com
sudo bash -c 'cat /etc/letsencrypt/live/example.com/fullchain.pem \
/etc/letsencrypt/live/example.com/privkey.pem \
> /etc/haproxy/certs/example.com.pem'
sudo haproxy -c -f /etc/haproxy/haproxy.cfg
sudo systemctl enable --now haproxyHigh Availability with Keepalived (VRRP)
Run two Linux load balancers with a Virtual IP (VIP) that fails over automatically. Keepalived uses VRRP (protocol 112) to elect a MASTER and BACKUP. If the primary fails—or HAProxy stops—the VIP moves to the backup in seconds.
# Install
sudo apt install -y keepalived # or: sudo dnf install -y keepalived
# /etc/keepalived/keepalived.conf (on primary)
vrrp_script chk_haproxy {
script "killall -0 haproxy"
interval 2
weight -30
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass StrongPass
}
virtual_ipaddress {
10.0.0.10/24 dev eth0
}
track_script {
chk_haproxy
}
}Use the same config on the backup node but set state BACKUP and a lower priority (e.g., 100). Open VRRP (protocol 112) between the LBs in your firewall or security group.
Session Persistence (Sticky Sessions)
- HAProxy: cookie-based stickiness (recommended for web apps)
- Nginx OSS: ip_hash (basic, IP-based; may be inaccurate behind NAT or CDNs)
- Stateless apps: prefer no stickiness; use shared session stores (Redis, database) when needed
Health Checks, Monitoring, and Logging
- HAProxy health checks: option httpchk, http-check expect, mark down failed nodes automatically
- Stats and metrics: HAProxy stats page (:8404), Prometheus exporters, syslog
- Nginx: access/error logs, stub_status module for basic metrics
- External uptime checks: curl, Pingdom, UptimeRobot, or k6/wrk for load testing
Performance Tuning for Linux Load Balancers
Apply sane kernel and process limits to handle spikes and keep latency low.
# /etc/sysctl.d/99-lb.conf
net.core.somaxconn = 65535
net.ipv4.ip_local_port_range = 1024 65000
net.ipv4.tcp_fin_timeout = 15
net.ipv4.tcp_tw_reuse = 1
fs.file-max = 1000000
sudo sysctl --system
# Raise open files limit
echo "* soft nofile 100000" | sudo tee -a /etc/security/limits.conf
echo "* hard nofile 100000" | sudo tee -a /etc/security/limits.conf- Nginx: use reuseport on listen, enable keepalive to backends
- HAProxy: tune.maxaccept, nbthread (modern HAProxy uses threads), http-reuse safe, reasonable timeouts
- Scale horizontally: add more LB nodes with Keepalived or anycast
Security Hardening
- Restrict management surfaces: bind stats to localhost or protect with auth and firewall
- Strong TLS: enable TLS 1.2/1.3, modern ciphers, HSTS, OCSP stapling
- Firewall: allow only 80/443 (and 8404 if required), permit VRRP (protocol 112) between LBs
- Sanitize headers: set X-Forwarded-* and strip hop-by-hop headers
- Rate limiting/WAF: HAProxy stick-tables or Nginx limit_req, add a WAF where needed
Testing and Troubleshooting
# Sanity checks
curl -I -H "Host: example.com" http://YOUR_LB_IP/
curl -I https://example.com/
# Validate configs
nginx -t
haproxy -c -f /etc/haproxy/haproxy.cfg
# Observe logs
sudo journalctl -u nginx -f
sudo journalctl -u haproxy -f
# Load testing (install first): wrk or ab
wrk -t4 -c200 -d60s https://example.com/Real-World Use Cases and Patterns
- WordPress at scale: HAProxy terminates TLS and load balances PHP-FPM/Nginx backends; media on object storage or CDN
- Blue/green deployments: drain a server from the pool, deploy, health-check, re-add
- Microservices gateway: route paths (/api/, /auth/) to different backends with L7 rules
- Hybrid L4+L7: IPVS for raw TCP scale, HAProxy for HTTP intelligence behind it
Don’t want to build this alone? YouStable’s managed hosting team routinely deploys HAProxy/Nginx load balancers with Keepalived, SSL automation, monitoring, and DDoS filtering—so you can focus on your app while we operate the edge.
Step-by-Step Summary: How to Use a Load Balancer on Linux Server
- Pick your stack: Nginx or HAProxy (L7), IPVS (L4) for extreme throughput
- Install on a Linux server; configure backends and routing algorithm
- Add health checks (HAProxy) and enable TLS offload
- Harden security and tune kernel/process limits
- Optionally add Keepalived for a VIP and automatic failover
- Test with curl and load tools; monitor logs and metrics
- Scale by adding backend servers or additional LB nodes
FAQs
Which is better for Linux load balancing: Nginx or HAProxy?
For most HTTP/HTTPS apps, HAProxy offers richer health checks, stickiness, and observability. Nginx is excellent as a simple reverse proxy and can be enough for many sites. If you need advanced L7 features, start with HAProxy; if you need simplicity, use Nginx.
How do I choose between Layer 4 and Layer 7 load balancing?
Choose L4 for maximum throughput with minimal logic (TCP/UDP services). Choose L7 when you need HTTP-aware routing, SSL termination, header-based rules, caching, or WAF integrations. Many large deployments combine both.
How do I enable sticky sessions on a Linux load balancer?
In HAProxy, use cookie insertion in the backend and set a cookie per server. In Nginx OSS, use ip_hash (basic) or move sessions to a shared store (Redis) to avoid stickiness. Cookie-based persistence is usually more reliable than IP-based.
Can I terminate SSL/TLS on the load balancer?
Yes. Terminate TLS at HAProxy or Nginx and forward plaintext to backends, or re-encrypt to backends if required. Use Let’s Encrypt automation and strong TLS settings (TLS 1.2/1.3, modern ciphers, HSTS).
How do I achieve high availability for the load balancer itself?
Run two Linux load balancers and use Keepalived (VRRP) to float a Virtual IP. Health checks ensure automatic failover if the primary node or process fails. Ensure VRRP (protocol 112) is allowed between the nodes and test failover regularly.