Linux operating system architecture is a layered design that separates the kernel (core) from user space (applications, libraries, and services). The kernel manages hardware, memory, processes, filesystems, and networking, while user space interacts with it via system calls and libraries. This modular approach makes Linux secure, scalable, and flexible across devices and servers.
Understanding the architecture of the Linux operating system helps you troubleshoot performance issues, secure servers, and build reliable applications. In this guide, we’ll break down kernel space vs user space, key subsystems like process scheduling and memory management, the boot process, containers, and real-world hosting scenarios.
What Is Linux Operating System Architecture?
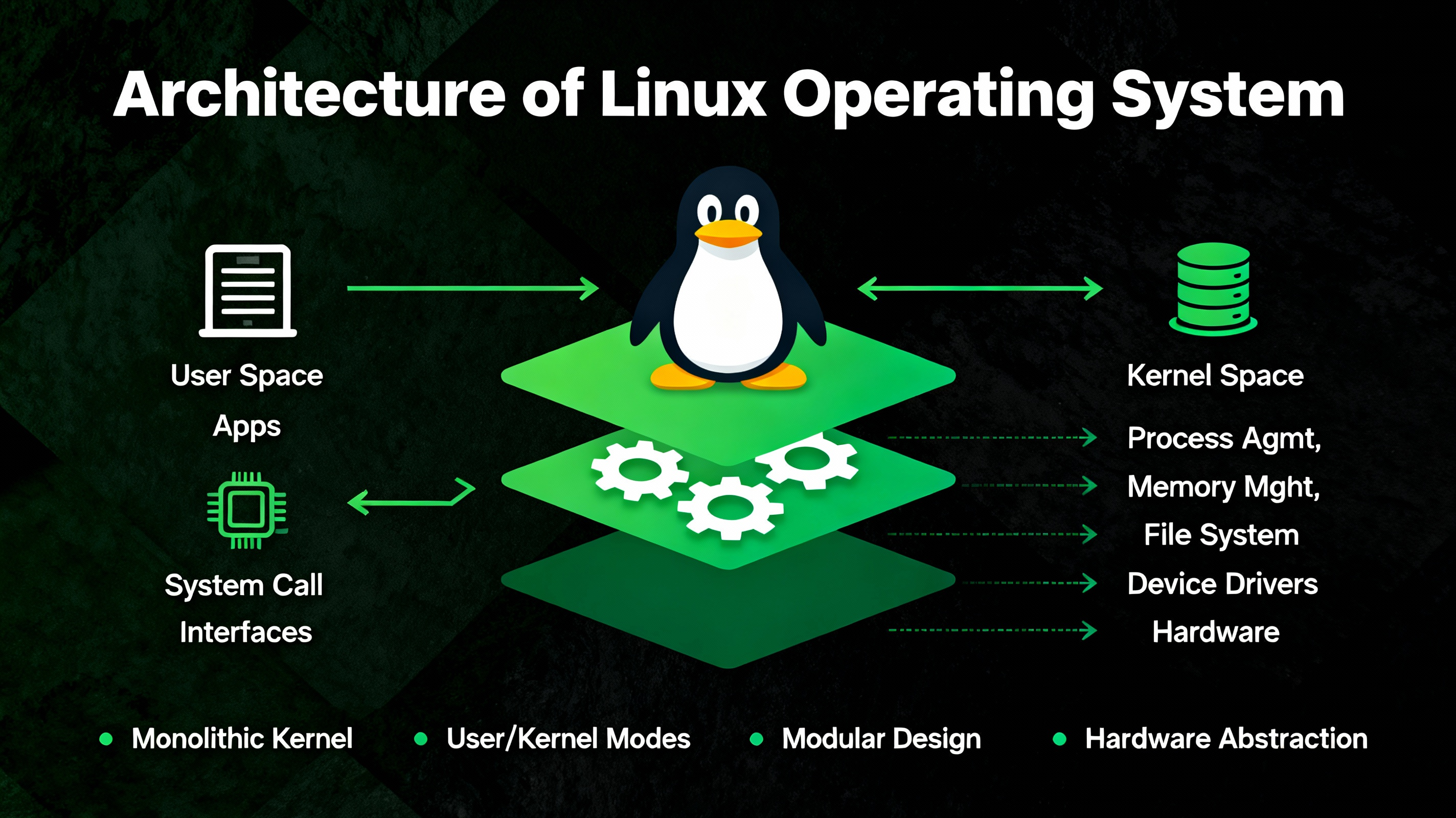
Linux operating system architecture describes how the OS is organized into interacting layers: the kernel (core), system libraries, user processes, and system services. Linux uses a monolithic kernel with loadable modules, meaning the core runs in privileged mode while drivers and features can be added dynamically without rebooting.
High-Level Components: Kernel Space vs User Space
Kernel Space
The kernel runs in ring 0 (privileged mode). It directly controls CPU scheduling, memory, device I/O, filesystems, and networking. Linux is a monolithic kernel, but its functionality is modular: device drivers, filesystems, and networking protocols can be loaded as modules at runtime.
Core kernel responsibilities include:
- Process management and scheduling (CFS: Completely Fair Scheduler)
- Memory management and virtual memory
- Virtual File System (VFS) layer and filesystem drivers (ext4, XFS, Btrfs)
- Networking stack (TCP/IP, firewalling with netfilter/iptables/nftables)
- Device drivers (storage, network, GPU, USB)
- Security: Linux Security Modules (SELinux, AppArmor), capabilities, namespaces, cgroups
User Space
User space runs in ring 3 (unprivileged mode). Applications call into the kernel via system calls, typically through the C standard library (glibc or musl). User space includes shells (bash, zsh), daemons (sshd, systemd services), utilities (coreutils), and package managers (apt, dnf, pacman).
Linux Boot Process and Init System
- Firmware (BIOS/UEFI) initializes hardware and hands off to the bootloader.
- Bootloader (GRUB, systemd-boot) loads the kernel and initramfs into memory.
- Kernel initializes drivers, mounts the root filesystem, and executes PID 1.
- Init system (usually systemd) brings up targets, services, sockets, and timers.
Modern distributions favor systemd for parallel service startup, dependency management, logging (journald), and unified service control. Alternatives include OpenRC, runit, and SysVinit.
Linux Kernel Subsystems Explained
1) Process Management and Scheduling
The scheduler (CFS) shares CPU time fairly across runnable processes, using per-CPU run queues and a red-black tree for efficient selection. Features include priority classes (nice values), real-time policies (SCHED_FIFO, SCHED_RR), and CPU affinity for pinning workloads to specific cores.
2) Memory Management
Linux uses virtual memory so each process sees its own address space. The kernel manages page tables, paging, NUMA (on multi-socket systems), transparent huge pages, and swap. Page cache and slab allocators optimize I/O and kernel object allocation respectively.
3) VFS and Filesystems
The Virtual File System abstracts filesystem operations (open, read, write, stat) and delegates to drivers for ext4, XFS, Btrfs, ZFS (out-of-tree), and network filesystems like NFS or SMB. Journaled filesystems (ext4, XFS) improve crash recovery and consistency.
4) Device Drivers
Drivers expose hardware as files under /dev and sysfs. Modules can be loaded dynamically to add or update device support without a reboot. Udev manages device nodes as hardware appears.
5) Networking Stack
The networking subsystem implements TCP/IP, routing, traffic control (tc), firewalling (iptables/nftables), VLANs, and advanced features like XDP and eBPF for high-performance packet processing and observability.
6) Security and Isolation
Linux Security Modules (SELinux, AppArmor) enforce mandatory access control. Capabilities split root privileges into fine-grained bits. Namespaces (UTS, PID, NET, IPC, MNT, USER) and cgroups v2 provide container isolation and resource quotas.
User Space Building Blocks
Libraries and Runtime
The C library (glibc, musl) wraps system calls and implements POSIX APIs. Other critical libraries include OpenSSL/LibreSSL for cryptography, libstdc++ for C++, and language runtimes (Python, Java, Go) that ultimately invoke syscalls through their standard libraries.
Shells, Utilities, and Package Managers
- Shells: bash, zsh, fish
- Core utilities: coreutils, findutils, grep, sed, awk
- Package managers: apt (Debian/Ubuntu), dnf (Fedora/RHEL), pacman (Arch), zypper (SUSE)
System Services and Daemons
Systemd units (service, socket, timer, path) standardize how daemons start, stop, and recover. Logs flow to journald by default, complemented by rsyslog or syslog-ng in many setups.
How User Space Talks to the Kernel: System Calls
Applications rarely invoke syscalls directly; they use library wrappers. On x86_64, the syscall instruction transitions from user mode to kernel mode, executing the requested service and returning a result or errno.
// Minimal C example: get process ID via a syscall wrapper
#include <stdio.h>
#include <unistd.h>
int main(void) {
printf("PID: %d\n", getpid());
return 0;
}You can inspect syscalls a program makes using strace:
# Trace file operations
strace -e trace=openat,read,write -f ./your_programLinux Filesystem Hierarchy (FHS) at a Glance
- / (root): top-level directory
- /bin, /sbin: essential user and system binaries
- /usr: userland programs and libraries (non-essential for early boot)
- /lib, /lib64: shared libraries
- /etc: system configuration
- /var: variable data (logs, spool)
- /home: user directories
- /proc, /sys: virtual filesystems exposing kernel and device state
- /dev: device nodes
- /run: volatile runtime data
Isolation and Resource Control: Users, Namespaces, and Cgroups
Linux enforces permissions through users, groups, and ACLs. Capabilities allow granting targeted privileges (e.g., CAP_NET_ADMIN) instead of full root. Namespaces isolate resources for containers, and cgroups v2 apply CPU, memory, and I/O limits.
- Namespaces: isolate PID trees, networking (veth, bridges), mounts, users, hostnames.
- Cgroups: throttle or guarantee resources; enable quotas and accounting.
- SELinux/AppArmor: restrict process capabilities and file access paths.
From Embedded to Cloud: Why Linux Scales
- Modular kernel: add or remove features via modules and configuration
- Broad hardware support: ARM, x86_64, RISC-V, and more
- Efficient networking stack with eBPF/XDP for high throughput
- Container-native: namespaces, cgroups, and overlay filesystems underpin Docker and Kubernetes
That flexibility makes Linux the de facto choice for servers, appliances, smartphones, and supercomputers alike.
Linux Architecture in Web Hosting: Practical View
In hosting, understanding Linux internals directly impacts uptime and performance. A typical LAMP/LEMP stack layers services over the kernel:
- Web server: Nginx or Apache (event or worker models)
- Application runtime: PHP-FPM, Node.js, Python (uWSGI/Gunicorn)
- Database: MySQL/MariaDB or PostgreSQL
- Security: firewall (nftables), fail2ban, TLS with OpenSSL
Tuning often involves sysctl parameters (kernel networking and memory), process limits, and I/O scheduling based on workload.
# Example: kernel networking tuning for many concurrent connections
sysctl -w net.core.somaxconn=1024
sysctl -w net.ipv4.tcp_tw_reuse=1
sysctl -w net.ipv4.ip_local_port_range="1024 65000"At YouStable, our managed Linux hosting stacks apply vetted kernel and service configurations, proactive monitoring, and isolation with cgroups and hardened policies—so your WordPress and SaaS workloads stay fast and secure without you touching low-level internals.
Common Misconceptions About Linux Architecture
- “Linux is a microkernel.” No—Linux is monolithic, but modular via LKM (Loadable Kernel Modules).
- “Root is all or nothing.” Capabilities and MAC (SELinux/AppArmor) allow granular control.
- “Containers are VMs.” Containers share the host kernel; VMs emulate hardware and run their own kernel.
- “All filesystems behave the same.” Different filesystems excel at different workloads (e.g., XFS for large files, Btrfs for snapshots).
Troubleshooting by Layer: Tools That Map to the Architecture
- Processes/Scheduling: top, htop, ps, chrt, taskset
- Memory: free, vmstat, smem, /proc/meminfo, perf mem
- Filesystems/I/O: iostat, iotop, df, du, lsof, mount
- Networking: ss, ip, ethtool, tcpdump, nft, tc
- Kernel logs and modules: dmesg, journalctl -k, lsmod, modprobe
- Security: getenforce/setenforce (SELinux), aa-status (AppArmor), capsh
Diagnose issues by moving from user space to kernel space: check application logs, then service state, then kernel messages and resource limits.
Monolithic vs Microkernel: Quick Comparison
- Monolithic (Linux): high performance, lower context-switch overhead; requires careful development to avoid kernel bugs.
- Microkernel (e.g., Minix): strong isolation, simpler core; potential performance overhead from message passing.
Linux’s approach, combined with modules and strong isolation features, offers a practical balance for real-world workloads.
Real-World Examples: Architecture in Action
- High-traffic web server: increase somaxconn, optimize Nginx workers to CPU cores, enable HTTP/2, and use eBPF-based observability to pinpoint kernel hotspots.
- Database server: tune dirty ratios and I/O scheduler, use XFS for large files, pin CPU affinity for predictable performance.
- Container platform: isolate tenant workloads with namespaces and cgroups; enforce SELinux; use overlayfs for fast image layering.
If you prefer not to manage these layers yourself, YouStable’s managed VPS and cloud hosting platforms ship with sane defaults and kernel-level hardening, freeing you to focus on your app.
Best Practices for Beginners
- Learn the basics of systemd: systemctl status/start/stop and journalctl for logs.
- Understand permissions, users, groups, and sudo; avoid logging in as root.
- Monitor resources with top/htop, free, df, and ss to find bottlenecks.
- Keep kernels updated for security and hardware support.
- Use SELinux/AppArmor in enforcing mode once you understand policy basics.
FAQs: Linux Operating System Architecture
What are the main components of Linux architecture?
The main components are the kernel (process, memory, filesystem, device, and network management), system libraries (glibc/musl), user processes and shells, and system services managed by an init system like systemd.
Is Linux a monolithic or microkernel?
Linux is a monolithic kernel with loadable modules. It runs core services in kernel space for performance, while allowing features like drivers and filesystems to be added dynamically as modules.
How do containers work on Linux?
Containers use namespaces to isolate resources (PID, NET, MNT, etc.) and cgroups to control resource usage. They share the host kernel but have separate views of filesystems, processes, and networks, enabling lightweight isolation compared to VMs.
What is the role of systemd in Linux?
Systemd is the init system and service manager. It starts services in parallel, manages dependencies, handles logging (journald), provides timers and sockets, and centralizes service control via systemctl.
Which filesystem should I choose: ext4, XFS, or Btrfs?
Ext4 is stable and versatile; XFS excels with large files and parallel I/O; Btrfs offers snapshots and checksums with modern features. Choose based on workload: databases often use XFS, general-purpose servers use ext4, and snapshot-heavy systems can benefit from Btrfs.
How do system calls work in Linux?
Applications request kernel services by invoking system calls, typically through the C library. The CPU switches from user mode to kernel mode, executes the syscall handler, and returns a result or error code to user space.
Do I need to tune the kernel for hosting workloads?
Default settings work for small sites, but high-traffic workloads benefit from tuning networking (somaxconn, backlog), file descriptors, and memory. Managed hosting from YouStable applies proven sysctl and service configurations out of the box.
Final Word
By mastering the Linux operating system architecture—from kernel subsystems to user space tools—you’ll troubleshoot smarter, secure better, and deploy faster. And if you want expert-tuned Linux hosting, YouStable can help you launch with confidence.


