IPTables is a powerful tool for configuring and managing the firewall on Linux servers. System administrators often need to fix IPTables when troubleshooting issues or adjusting rules that control incoming and outgoing network traffic. However, improper configurations, conflicting rules, or service failures can cause IPTables to misbehave, potentially leading to network issues or security risks.
In this guide, we’ll cover common IPTables issues on Linux servers and provide step-by-step solutions to fix them. Whether you’re dealing with service failures, misconfigured rules, or network connectivity issues, we’ll help you resolve the problem and restore the firewall’s functionality.
Preliminary Steps Before Fixing IPTables
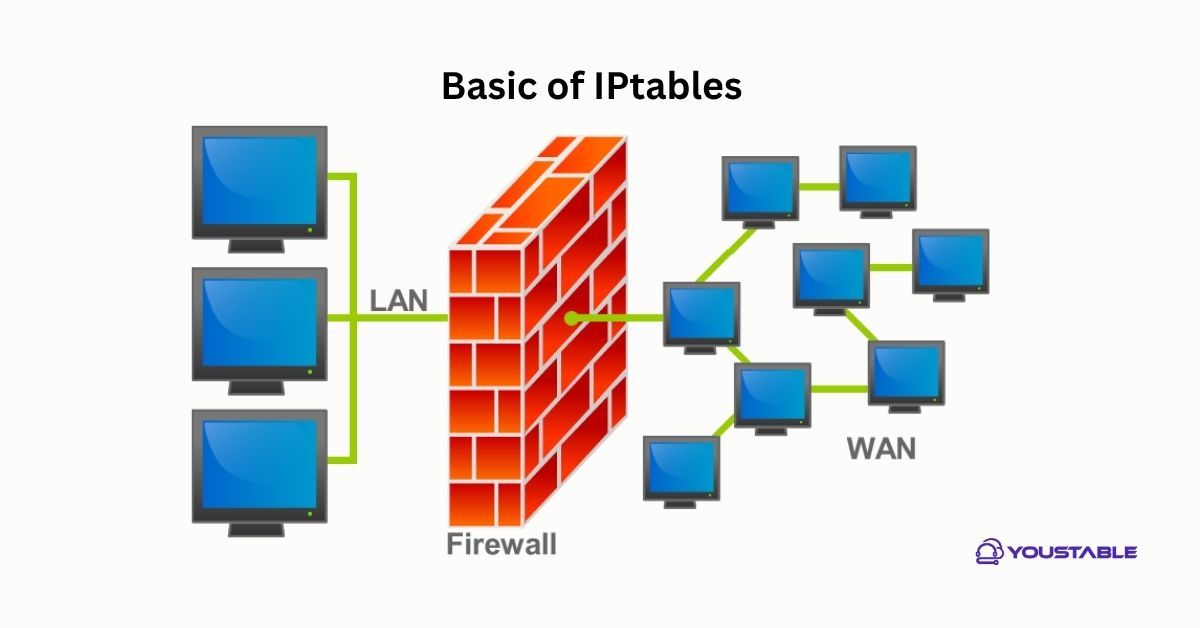
Before troubleshooting, ensure that IPTables is installed and running properly on your server.
Verify IPTables Installation
Check if IPTables is installed on your system:
iptables --versionIf IPTables is not installed, you can install it using the following commands:
For Debian/Ubuntu-based systems:
sudo apt-get install iptablesFor RHEL/CentOS-based systems:
sudo yum install iptablesCheck the IPTables Service Status
To check the status of IPTables, use the following command:
For Debian/Ubuntu-based systems:
sudo systemctl status iptablesFor RHEL/CentOS-based systems:
sudo systemctl status iptablesIf the service is not running, start it:
For Debian/Ubuntu-based systems:
sudo systemctl start iptablesFor RHEL/CentOS-based systems:
sudo systemctl start iptablesTo ensure IPTables starts automatically at boot:
For Debian/Ubuntu-based systems:
sudo systemctl enable iptablesFor RHEL/CentOS-based systems:
sudo systemctl enable iptablesCheck IPTables Rules
To view the current IPTables rules, use the following command:
sudo iptables -LThis will display the list of active rules for the firewall. If necessary, examine the rules to see if anything looks incorrect or overly restrictive.
Identifying Common IPTables Issues
Several issues may arise when using IPTables on a Linux server, including service failures, misconfigured rules, or blocking necessary network traffic. Below are some common problems and their causes:
- IPTables Blocking Legitimate Traffic
A common problem with IPTables is accidentally blocking legitimate traffic, such as HTTP/HTTPS, SSH, or DNS queries, due to overly strict rules.
- IPTables Service Not Starting
If the IPTables service is not running, it could be due to misconfiguration or issues with the firewall service itself.
- IPTables Rules Not Persisting After Reboot
On some systems, changes to IPTables rules may not persist after a reboot. This can be due to IPTables not being saved or a configuration issue.
- Misconfigured NAT or Port Forwarding Rules
If you are running a web server, game server, or VPN on your VPS, port forwarding and NAT rules are essential. Misconfigured rules may prevent the server from receiving incoming traffic on specific ports.
- Conflicting Rules or Incorrect Chain Settings
Sometimes, IPTables rules can conflict with one another or fail to execute in the correct order, leading to unintended blocking or allowing of network traffic.
Fixing IPTables on Linux Server: Step-by-Step Solutions
Let’s go through common IPTables issues and solutions to fix them.
Check and Fix IPTables Rules for Blocking Legitimate Traffic
If legitimate traffic is being blocked, it’s likely due to misconfigured rules. Common culprits include blocking HTTP/HTTPS (ports 80 and 443) or SSH (port 22).
- Allow HTTP/HTTPS and SSH Traffic:
To ensure HTTP, HTTPS, and SSH traffic is allowed, use the following commands: For HTTP (port 80):
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPTFor HTTPS (port 443):
sudo iptables -A INPUT -p tcp --dport 443 -j ACCEPTFor SSH (port 22):
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT- Save Changes:
After adding the necessary rules, make sure to save the rules so they persist across reboots:
For Debian/Ubuntu-based systems:
sudo iptables-save > /etc/iptables/rules.v4For RHEL/CentOS-based systems, you can save the rules using the service command:
sudo service iptables save- Restart IPTables:
After making changes to IPTables, restart the service to apply the new rules:
sudo systemctl restart iptablesRestart the IPTables Service
If the IPTables service is not running or seems to be misbehaving, restarting the service can often resolve the issue.
To restart IPTables:
sudo systemctl restart iptablesThen, check the status again to ensure it’s running:
sudo systemctl status iptablesCheck for IPTables Configuration Conflicts
If you’re experiencing issues where certain ports or services are not accessible, it might be due to conflicting or misconfigured rules. Ensure that the rules are defined in the correct order and that there are no conflicting rules.
- List All Rules:
Use the following command to display all current IPTables rules:
sudo iptables -L -v -nThis command will show verbose output with the rule counts and network addresses, which can help identify the root cause.
- Delete Conflicting Rules:
If you find conflicting rules, you can delete them with:
sudo iptables -D INPUT -p tcp --dport 22 -j DROPThis will delete the rule that blocks SSH traffic on port 22, for example.
Check for NAT or Port Forwarding Issues
If you’re running services that require port forwarding (such as a web server, VPN, or game server), make sure your NAT and port forwarding rules are correctly configured in IPTables.
- Enable IP Forwarding:
If you are setting up port forwarding or NAT (Network Address Translation), ensure that IP forwarding is enabled on your server. You can enable it by running:
sudo sysctl -w net.ipv4.ip_forward=1To make the change persistent across reboots, edit /etc/sysctl.conf:
sudo nano /etc/sysctl.confUncomment or add the following line:
net.ipv4.ip_forward = 1Then apply the changes:
sudo sysctl -p- Configure Port Forwarding:
If you’re using NAT or need to forward ports to a local machine behind the VPS, use the following rules: For forwarding TCP port 80 to an internal IP (e.g., 192.168.1.100):
sudo iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT --to-destination 192.168.1.100:80 sudo iptables -A FORWARD -p tcp -d 192.168.1.100 --dport 80 -j ACCEPT- Save the Changes:
After configuring port forwarding, save the rules:
For Debian/Ubuntu-based systems:
sudo iptables-save > /etc/iptables/rules.v4For RHEL/CentOS-based systems, save the configuration with:
sudo service iptables saveFix IPTables Rule Persistence
If your IPTables rules are not persisting across reboots, it’s possible that the rules are not being saved or loaded correctly.
- Save IPTables Rules:
To ensure your rules are saved and persist after a reboot, you can use the following commands:
For Debian/Ubuntu-based systems:
sudo iptables-save > /etc/iptables/rules.v4For RHEL/CentOS-based systems, you can save the rules using:
sudo service iptables save- Ensure IPTables Restores on Boot:
For Debian/Ubuntu, the rules are typically restored automatically using iptables-persistent. If necessary, install it:
sudo apt-get install iptables-persistentFor RHEL/CentOS, use the following command to ensure the rules are loaded on boot:
sudo systemctl enable iptablesCheck for Logging and Debugging
If you’re still facing issues, you can enable logging to see what traffic is being blocked or accepted by your firewall.
- Enable Logging for Dropped Packets:
To log dropped packets, use the following rule:
sudo iptables -A INPUT -j LOG --log-prefix "iptables dropped: " --log-level 4- View Logs:
Logs are typically stored in /var/log/syslog or /var/log/messages:
sudo tail -f /var/log/syslogConclusion
Fixing IPTables on a Linux server involves troubleshooting common issues such as service failures, misconfigured rules, and port forwarding problems. By following the steps outlined in this guide, you can address these issues and ensure your firewall is working as expected. Regularly check your firewall rules, monitor logs, and test network connectivity to maintain a secure and optimized environment for your Linux server.